Hot topic online right now is how Lenovo's shipped thousands of its computers with a pre-installed adware, called Superfish. Officially, it is supposed to insert ads as users browse the internet. Unofficially, it does much much more than that.
Superfish is able to insert ads on all webpages, including the secured HTTPS connections. How? It has unrestricted authority over creation of security certificates and therefore can inject permissions that lets it read data from the pages and inject appropriate ads. Yes, that includes all user communication with social networks, banks, shopping carts, and email. Such an attack is called the "Man in the Middle" attack--the malicious software reads the data right on the user's computer before it gets encrypted and sent out.
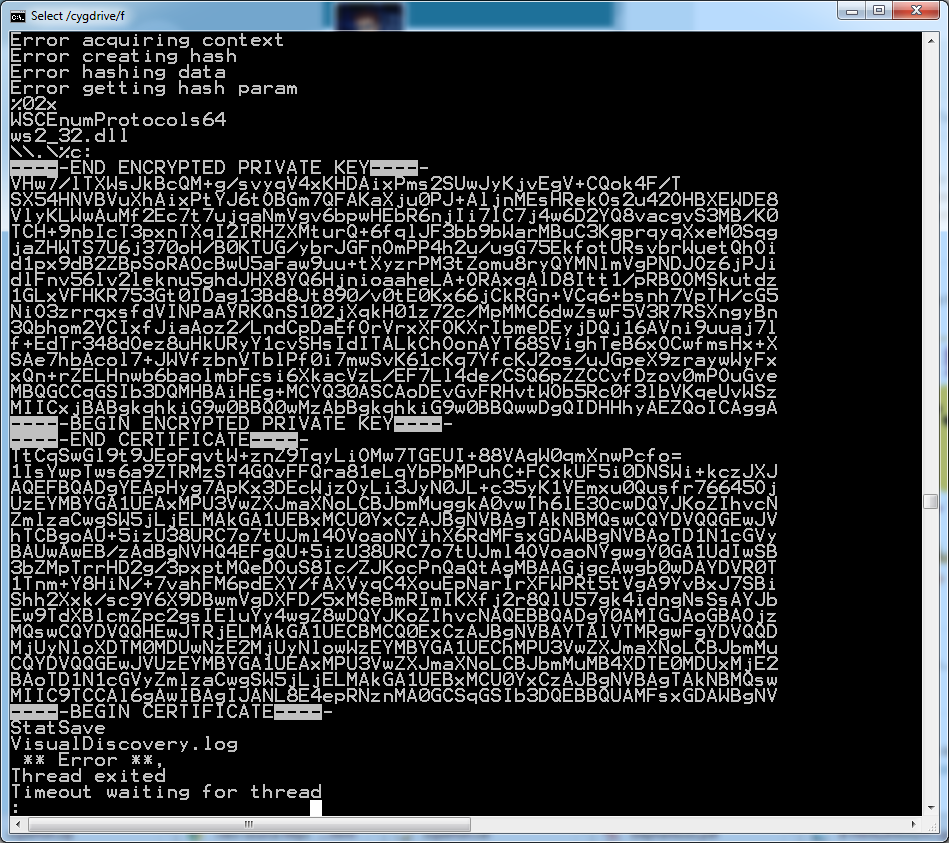
Needless to say, this backfired on Lenovo, who entered the partnership with Superfish not knowing all the details. Although Superfish claimed that it had been using its permission only to inject ads, a number of security researchers have already cracked Superfish's password key and posted proof (see screenshot below). This means that anyone who wants to generate fake security certificates can overload Superfish and abuse its permissions.
Lenovo has confirmed that Superfish disabled activation on existing machines in Jan'15. It has also been removed from new machines leaving the factory.
Source

No comments:
Post a Comment